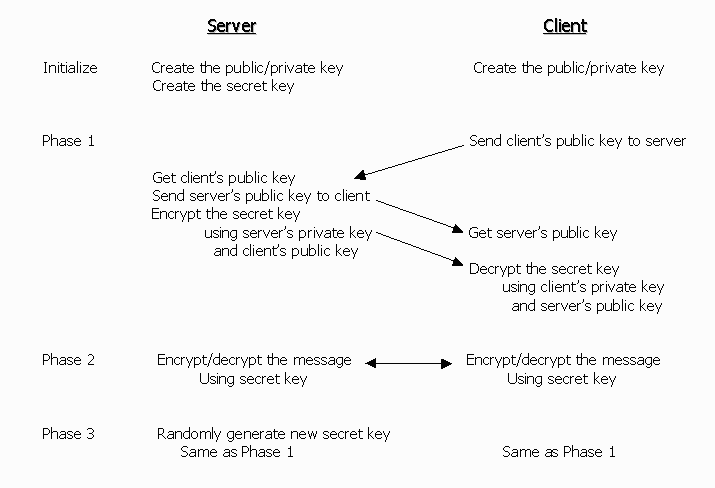
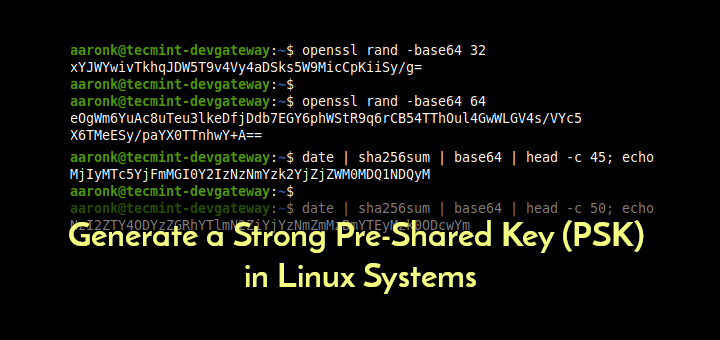
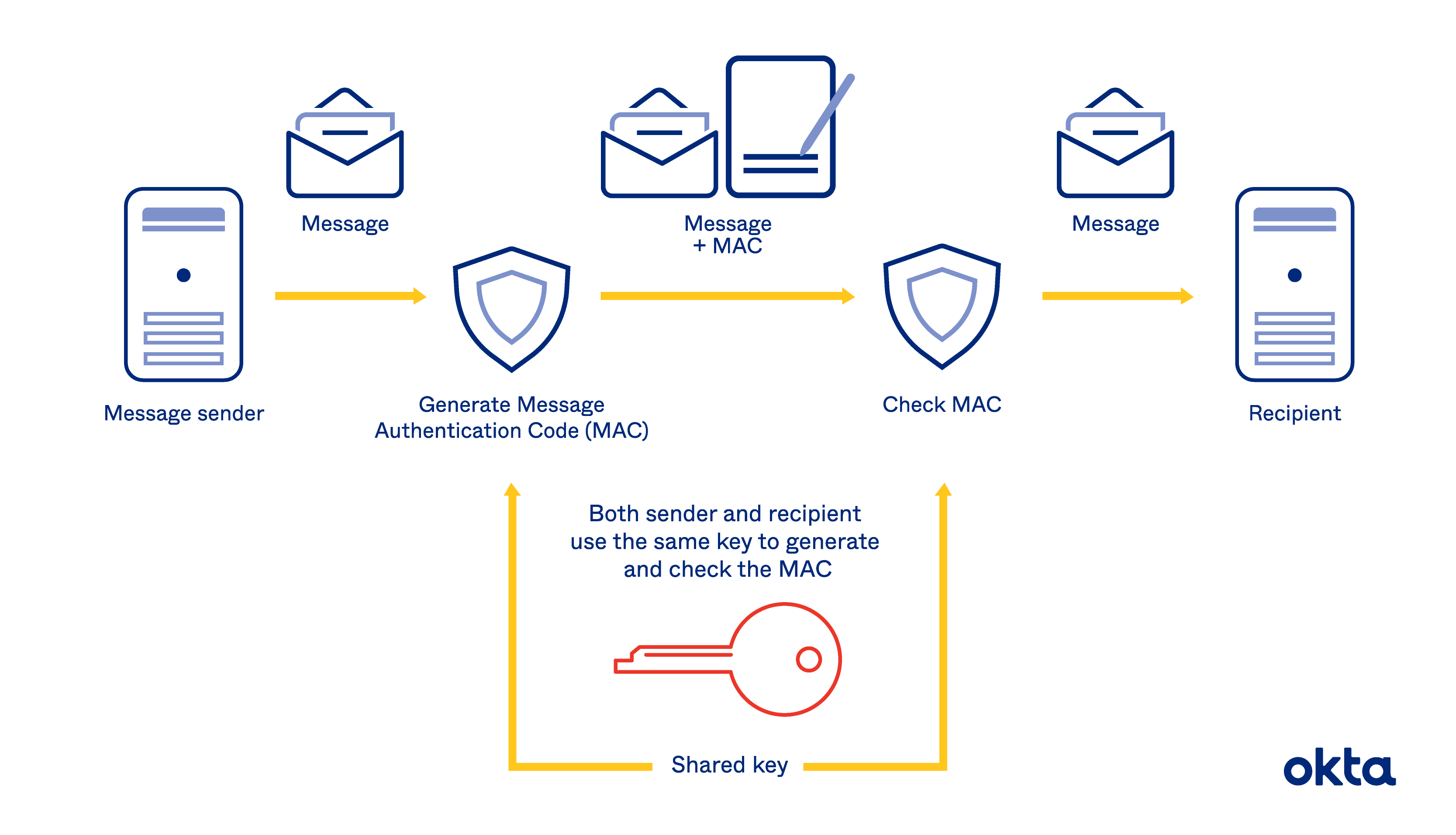
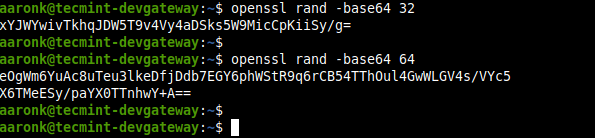
A novel RSA algorithm for secured key transmission in a centralized cloud environment - Ambika - 2020 - International Journal of Communication Systems - Wiley Online Library
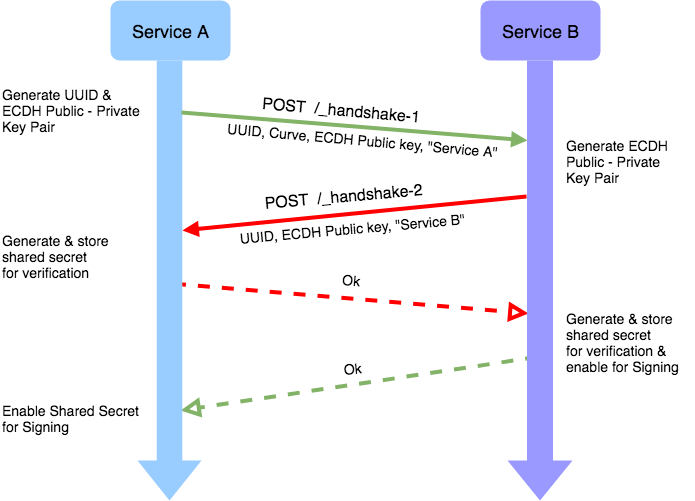
Inter-service authentication and the need for decentralised shared key exchange | by Krupa Sagar | Practo Engineering | Medium
![PDF] Comparison Studies between Pre-Shared key and Public Key Exchange Mechanisms for Transport Layer Security (TLS) | Semantic Scholar PDF] Comparison Studies between Pre-Shared key and Public Key Exchange Mechanisms for Transport Layer Security (TLS) | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/7439ef04b0ad0507f4cc0013c29e8778ff2da071/14-Figure2.2-1.png)