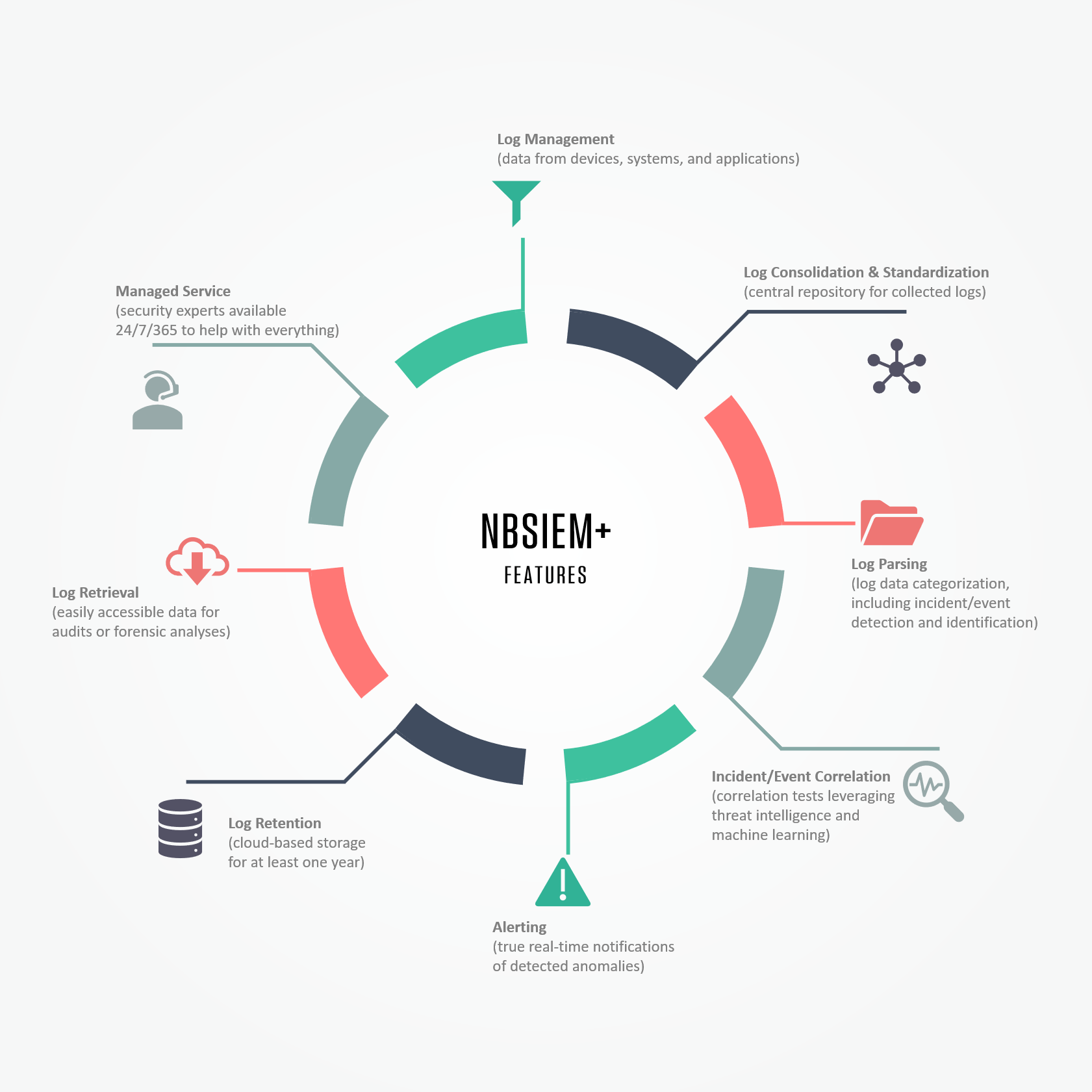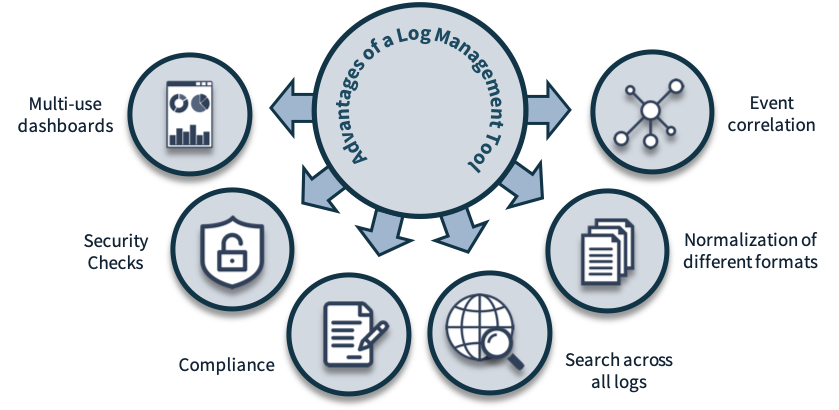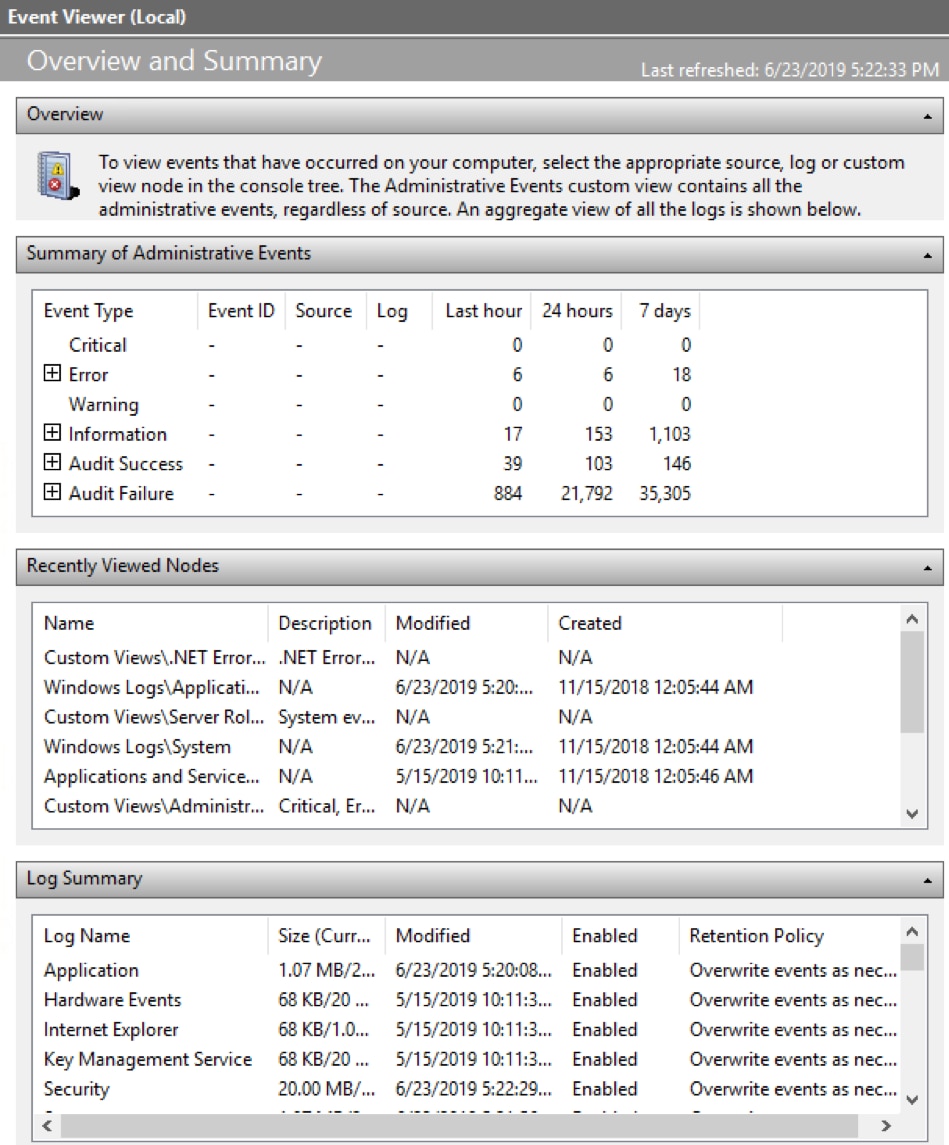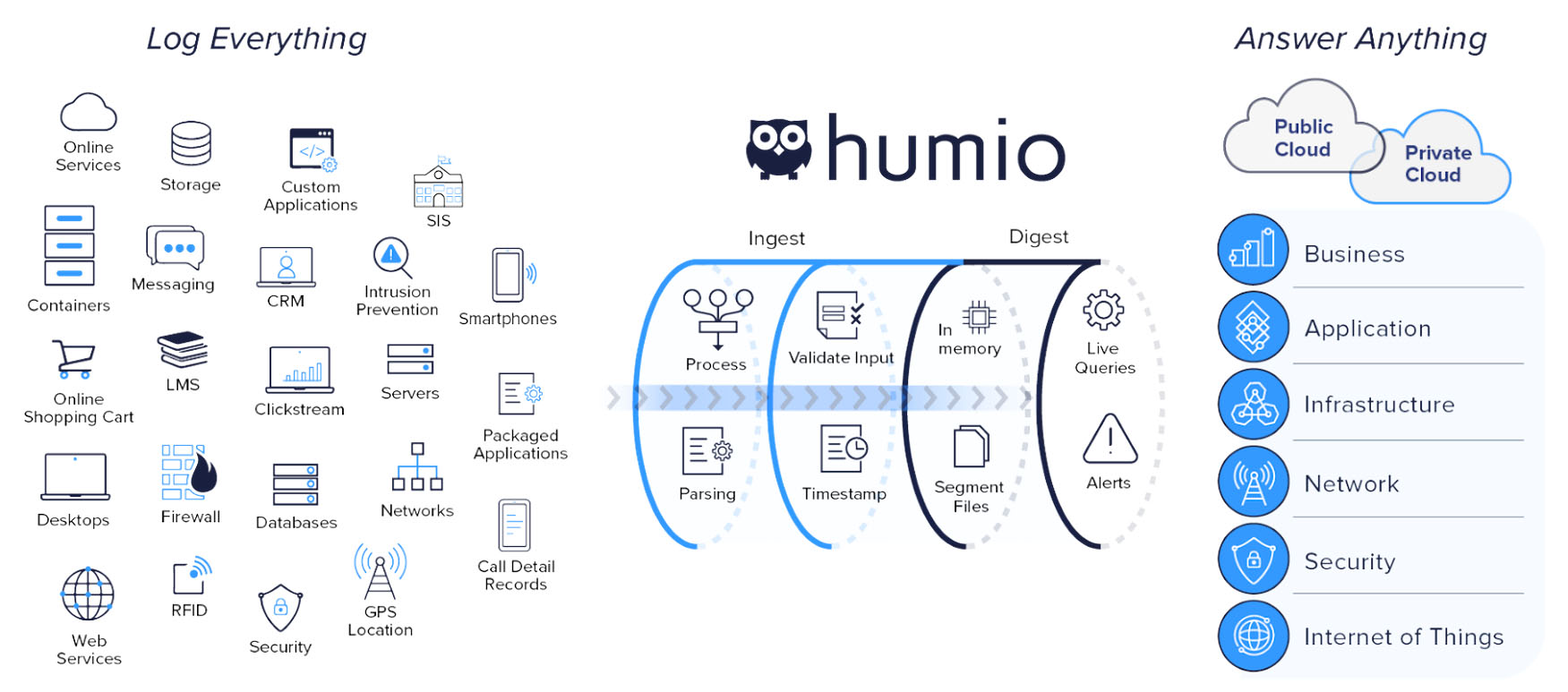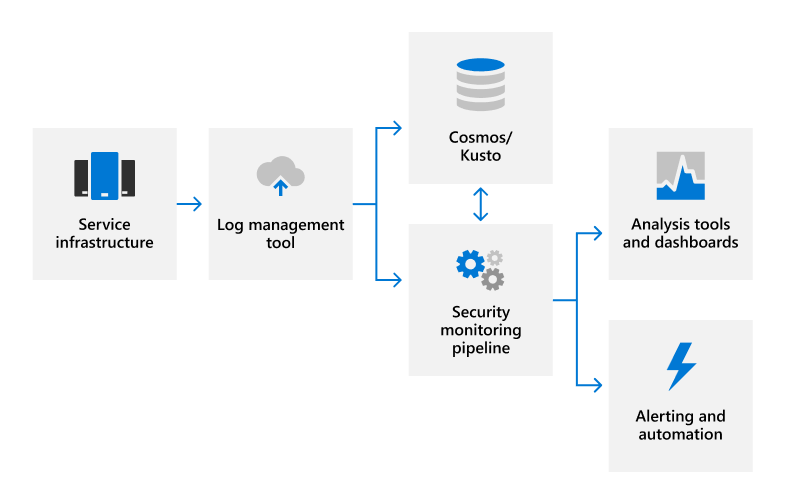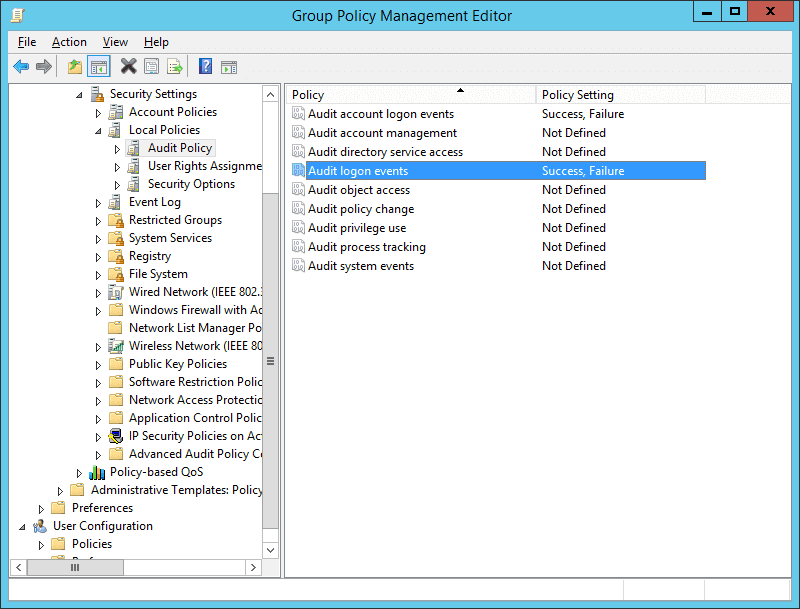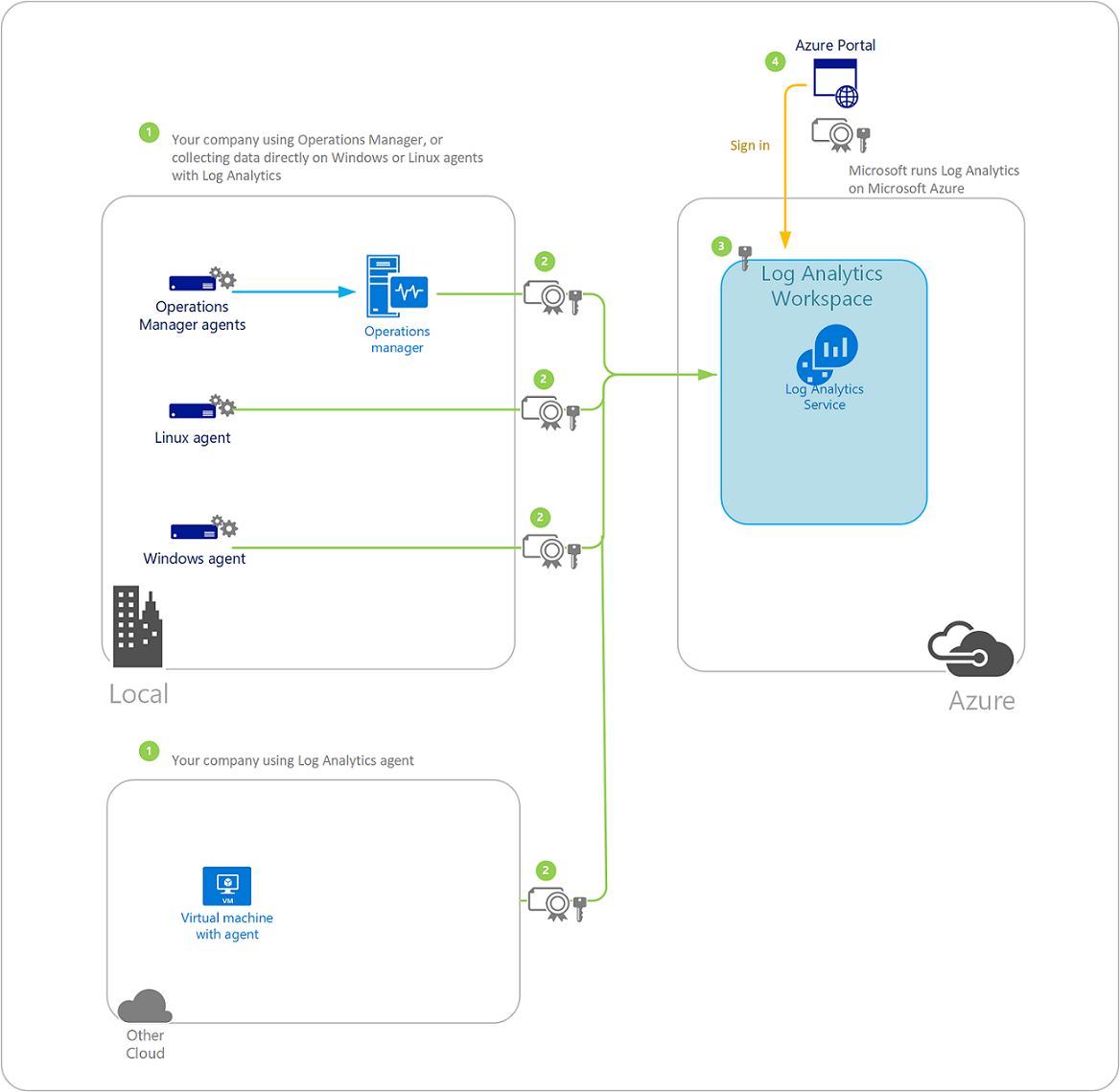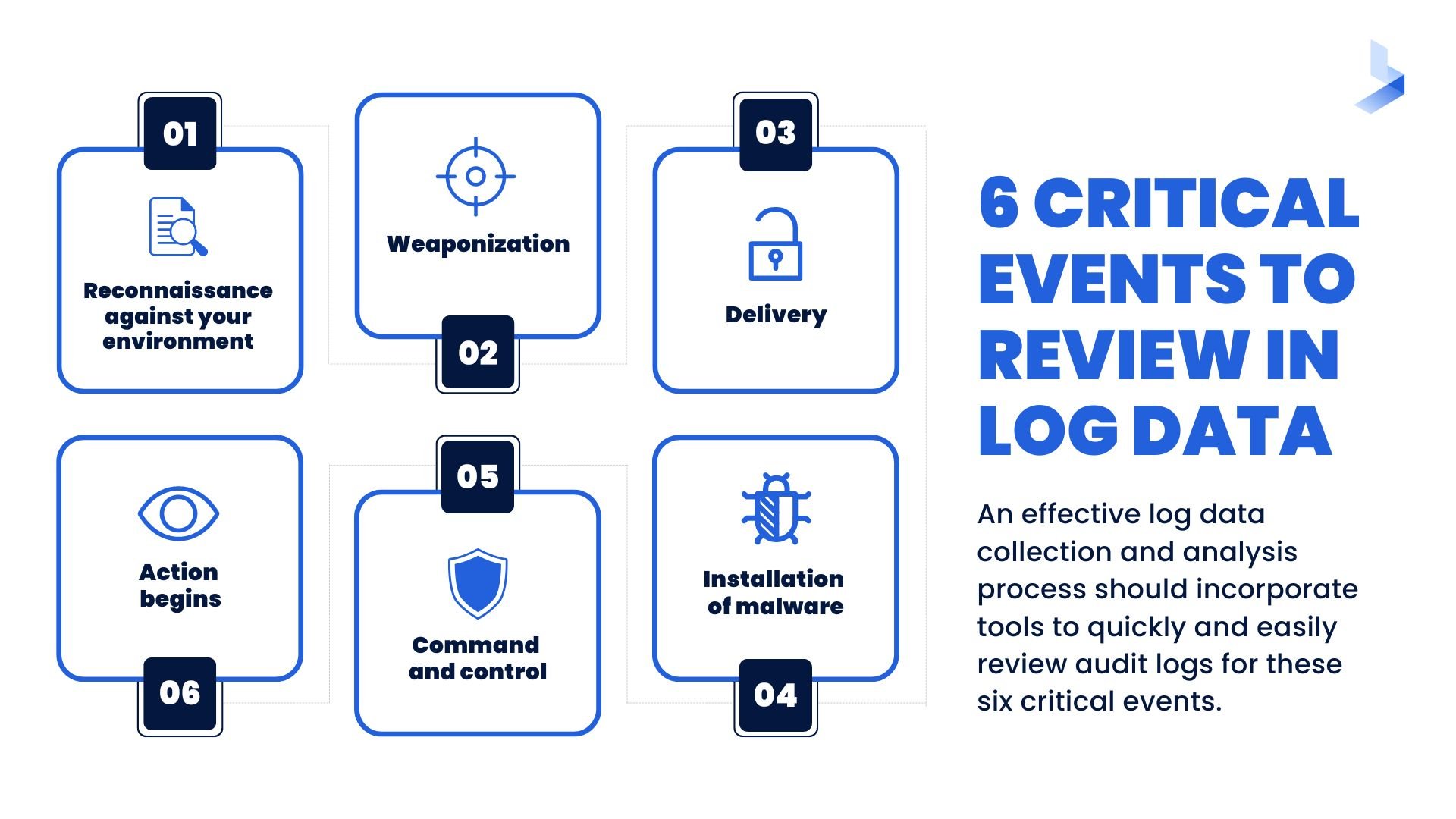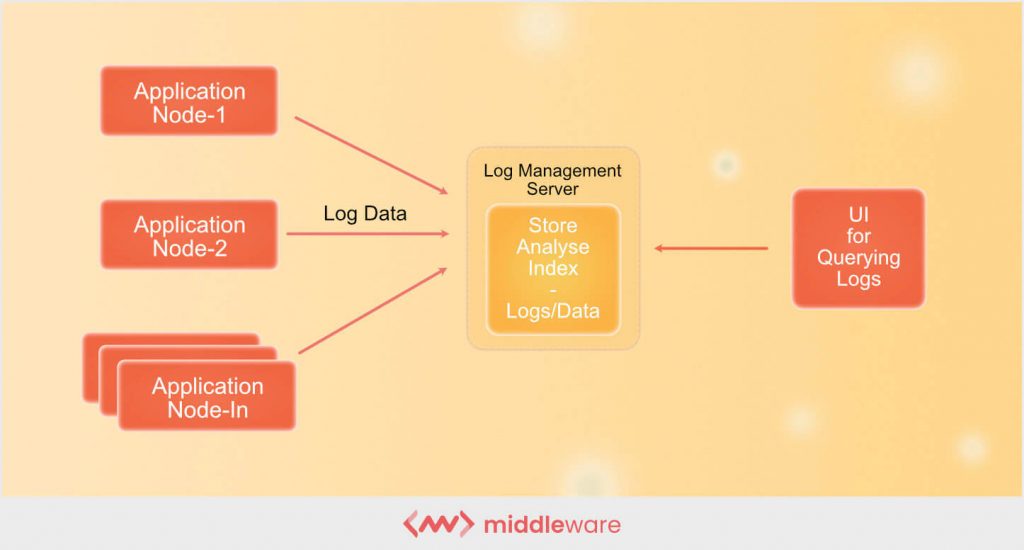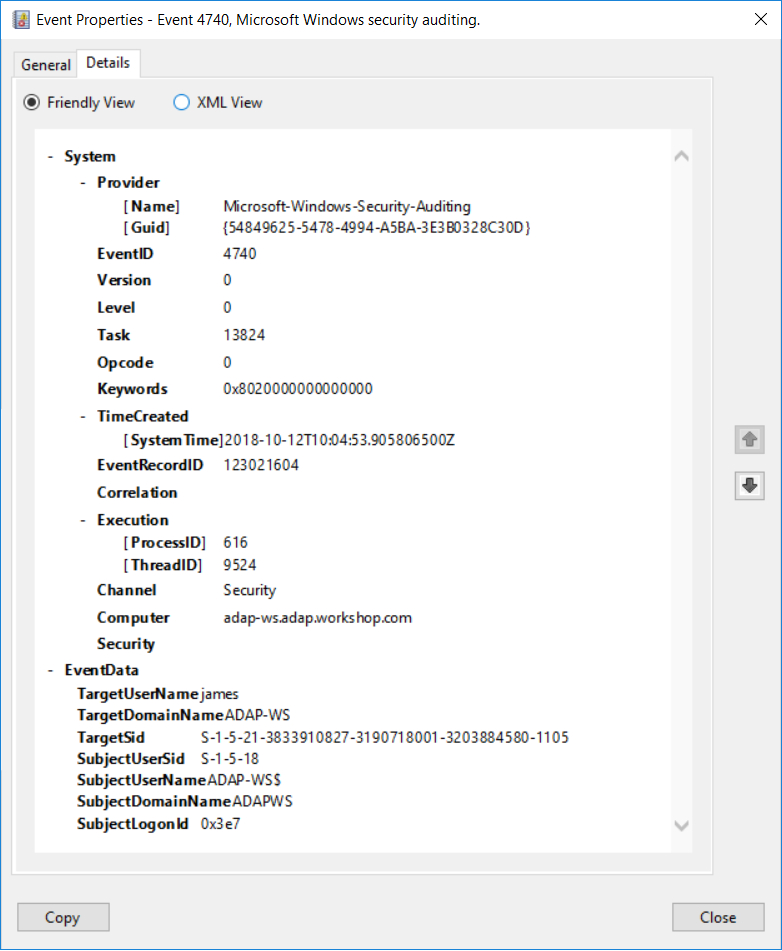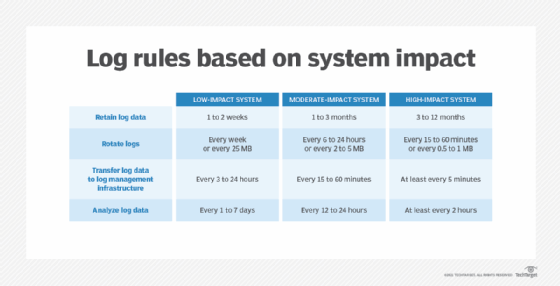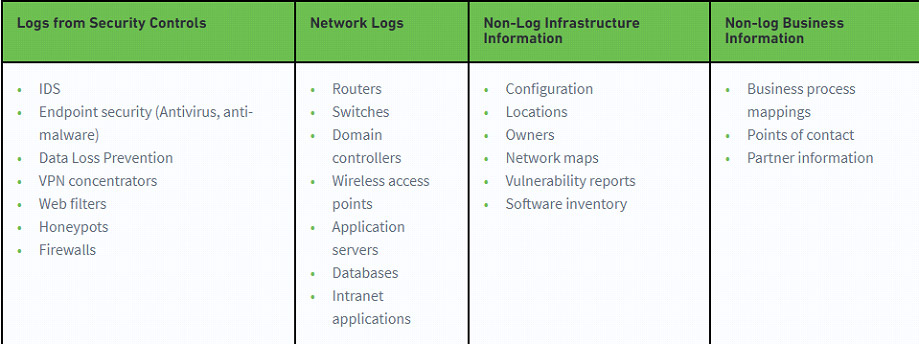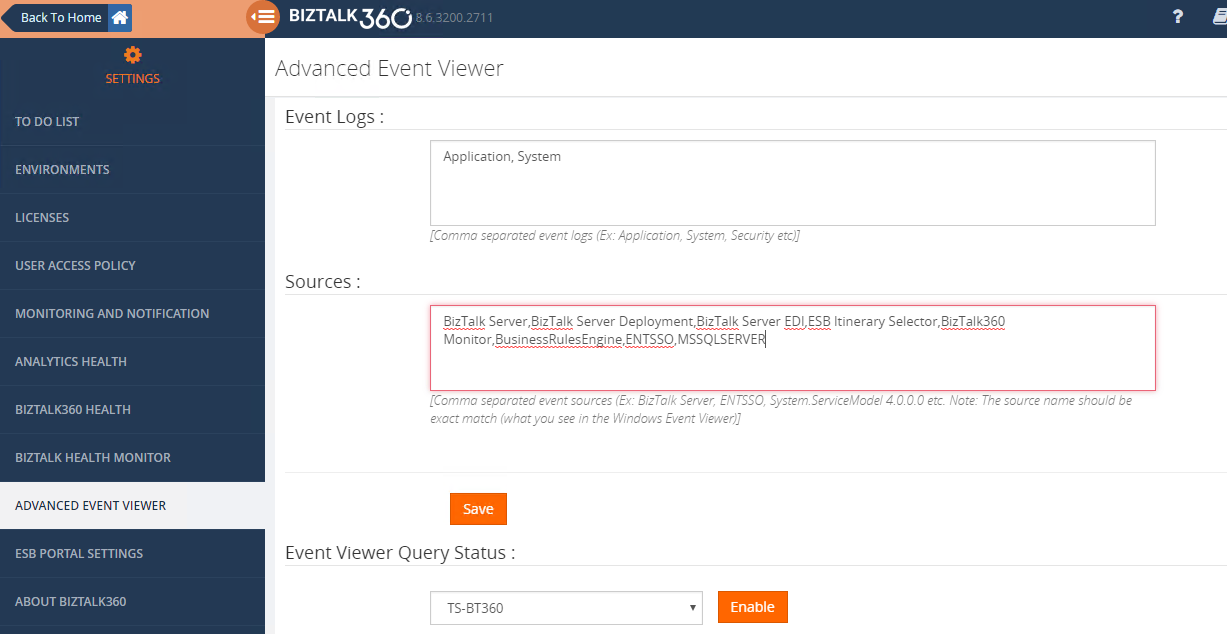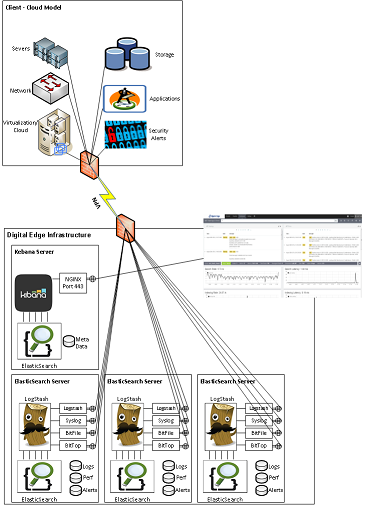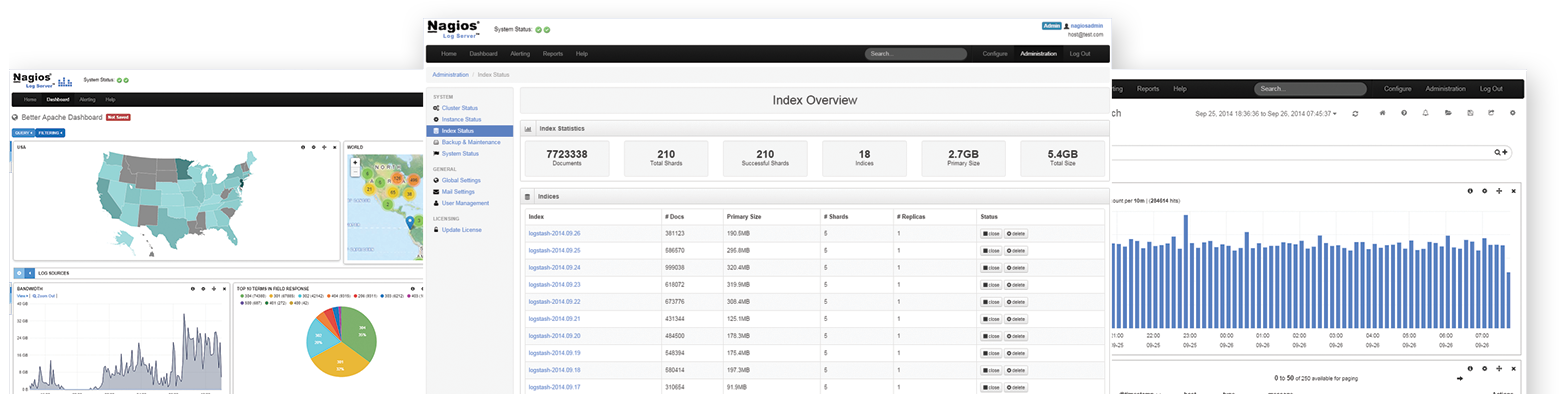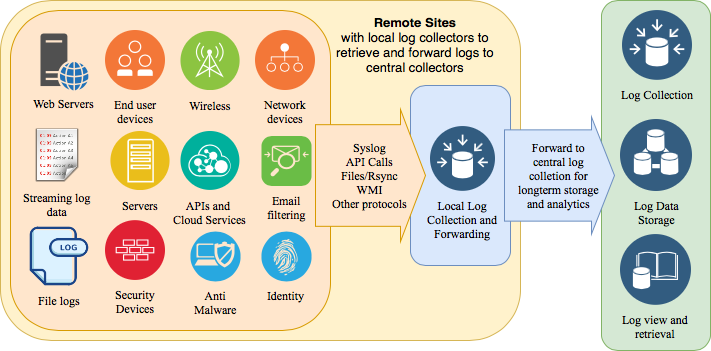
Security Operations Center (SOC): Prioritizing Log SourcesRafeeq Rehman | Cyber | Automation | Digital

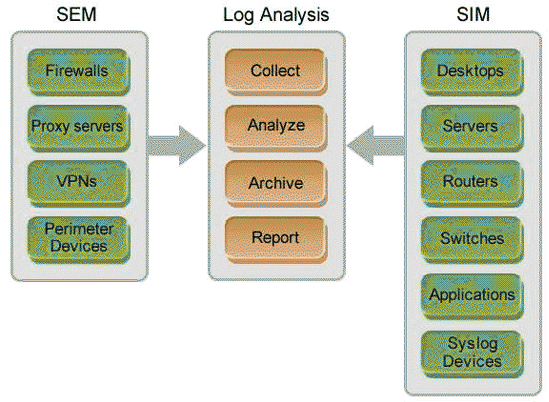
What Is Security Information and Event Management (SIEM)? Definition, Architecture, Operational Process, and Best Practices - Spiceworks